

A. Professional groups with statutory requirements for responsibility to protect their client conversations against unauthorized interception, such as clergy, healthcare, social services, teachers, counselors, psychologists, lawyers, bank officers and accountants. More information about the statutory duty of confidentiality can be read at: https://sv.wikipedia.org/wiki/Tystnadsplikt
B. Companies that are particularly vulnerable to eavesdropping and cyber attacks, for example are listed companies and/or companies that operate in banking and finance, payment services, insurance, the pharmaceutical industry, suppliers in the defense sector, telecom companies that handle customers' data and call traffic, and IT companies that directly or indirectly take care of other companies' internal IT security.
C. Critical activities within the public sector that procure more secure mobile telephony and data traffic according to LOU or LUFS.
Abuse of Arxlight Mobile is prevented by the fact that we only allow subscribers who can prove employment within a company, professional group or activity that justifies the need for increased protection against eavesdropping. Therefore, we reserve the right to refuse and the right to suspend users where such a need cannot be proven.
All mobile calls to and from unprotected landlines or mobile phones are encrypted from the Arxlight Mobile protected mobile phone through the insecure mobile network to the Arxlight Mobile Center and are then connected to a landline or mobile phone without encryption, meaning that interception directed at those who are at high risk of interception attempts is effectively protected up to the public telecommunications network.
Half-encryption is an effective protection in contact with parties who themselves have a low risk of unauthorized interception. Even information about who the other party to the conversation is is protected through the mobile network, meaning that mapping parties to the conversation for Arxlight Mobile users is considerably more difficult.
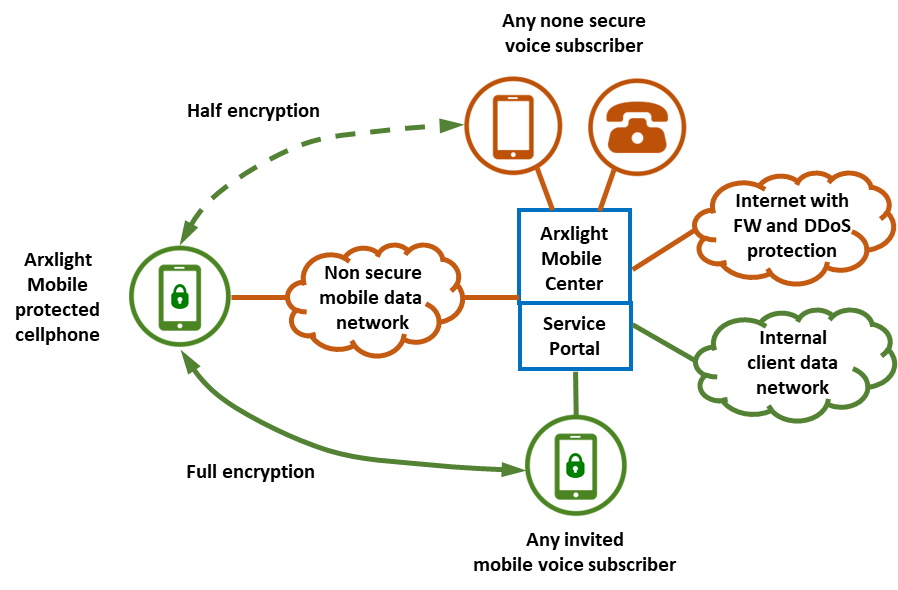
Arxlight Mobile has full encryption all the way between all users within the same organization and other organizations that also use Arxlight Mobile, even if different crypto keys are used.
Arxlight Mobile users can also invite their clients who need full encryption all the way to a limited free Arxlight Mobile service. Lawyers, priests, social services, banks and the defense industry are some examples of professional groups that may need to protect their client conversations all the way, as well as close family members who can be used to map people who have a higher risk of unauthorized interception.

To activate full encryption, the Arxlight Mobile subscriber invites their client to a limited client service via the Arxlight Mobile service portal, which then sends a mobile application to the client's mobile phone with an automated function test that quality ensures safe encryption all the way.
Free limited client service can be upgraded to full service upon application which includes suitability testing, as Arxlight Mobile is only offered to users who have a clear professional need for protection. We reserve an unlimited right to refuse new users and the right to suspend users if we believe this is justified.
Arxlight Mobile includes a protected mobile phone with a high level of security that significantly complicates traditional methods of hacking or eavesdropping, with subscriptions for 3G/4G/5G data and calls via the fixed telephone network (PSTN), as well as Internet and E-mail service.
Complete mobile exchange with commonly used exchange functions is also included. Fixed connection to own internal data network with relevant security levels is offered as an option upon request.

Municipalities, county councils, blue-light authorities and government works, as well as companies in power supply, telecom, transport and food supply are examples of socially critical operations that may need secure functionality for internal telephone calls, e-mail and reliable access to their own IT systems in the event of special events where national networks are disrupted, for example due to extreme weather and/or cyber attacks.
Arxlight Mobile can be supplemented with a customer-placed exchange if it ensures reliable and robust function for internal calls and IT functions within the own organization, via permanently installed access points that cover the company's workplaces and which work for internal calls, e-mail and IT functions even if national networks do not work.
Fortified internal telephony and mobile internal IT functions can also be delivered with protection against EMP with military weaponry that covers the entire system chain from protected mobile phone to customer-placed exchange with all intermediate network elements, as well as battery backup for long endurance from 1 week up to entire annual cycles with charging of batteries from sun, wind, fossil fuels and biofuels (for example easily available wood) which provides safe electricity supply 24 hours a day all days of the year, even when it is not windy or sunny.

Arxlight Mobile offers in Step 5 an option that significantly complicates unauthorized geolocation by anonymizing the user in open mobile networks, in such a way that the user becomes almost completely invisible to unauthorized people in all mobile networks.
The own organization can activate a well-protected geolocation that is only available internally if necessary, for example for security reasons for SOS calls.
Since effective protection against unauthorized geolocation requires a number of different collaborative measures, this level of protection is only offered to professional groups that have a clear need for protection against unauthorized geolocation, and each individual system solution is delivered with high confidentiality requirements.
As all mobile subscriptions are easy to geolocate for unauthorized people via mobile networks, effective protection against unauthorized geolocation and interception may also need to include protection against unauthorized geolocation for close family members and work colleagues, to avoid indirect tracking and/or interception through mobile phones used by people who are often seen in close proximity to people in need of protection against unauthorized geolocation via mobile networks.